- Email: [email protected]
- Fairfield, Connecticut
It is essential to adopt DevSecOps in the earlier stages of Software development life cycle(SDLC). Security breaches have become one of the most significant threats that governments and organizations face today.
CLICK HERE
A Secure SDLC requires adding security testing at each software development stage from design to deployment. Designing applications to ensure that your architecture will be secure, including security risk factors as part of the initial planning phase.
CLICK HERE
Threat modeling puts you in the mind of the attacher and allows us to see the application from the attacker’s eyes and block their future attacks. We can also use OWASP Threat Dragon and Cairis threat tools to create threat model diagrams
CLICK HERE
The Development stage starts with writing code and we can use shift-left security best practice which incorporates security thinking in the earliest stages of development.
Read More
We should scan our code for vulnerabilities. Static code analysis may detect a bug or a possible overflow in code which degrades the system performance by reducing the amount of memory available. Sometimes it can be used as an attack exploited by hackers
Read More
GitGuardian is an enterprise-friendly tool for detecting and preventing secrets in the code base. We can also scan the non-git tracked files. There are other tools as well like Gitleaks that are similar.
Read More

We help customers reduce risk while building the future of their businesses. The Cloud Native Security Platforms we use are the industry's most integrated Cloud Native Application Protection Platform (CNAPP), protecting the entire application lifecycle..
Our executive team has a total of 40 years of experience in the industry.




Working with Customers.
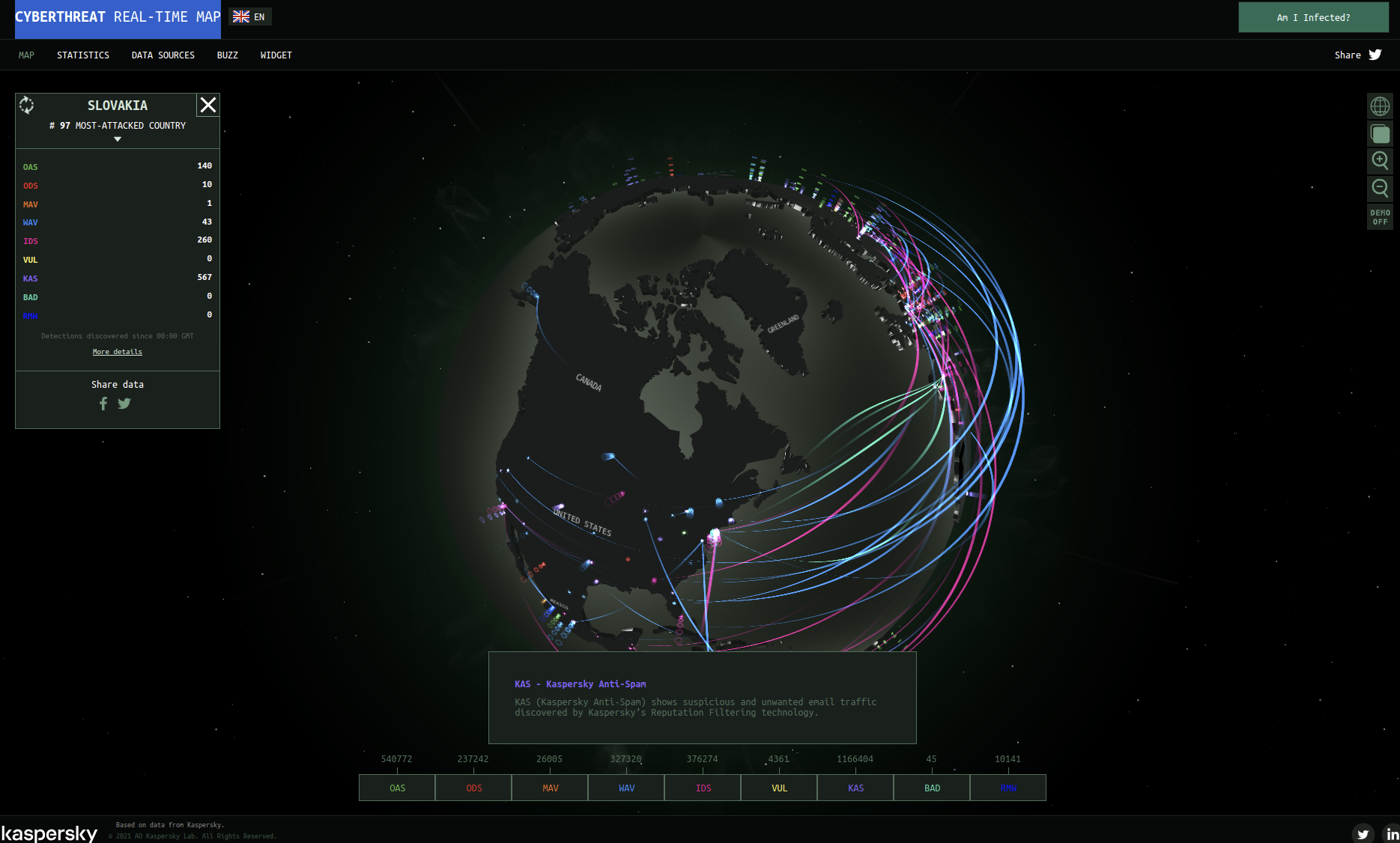
Kaspersky Lab presents its new interactive Cyberthreats Realtime Map. This visual tool allows users to see what is going on in cybersecurity around the world in real time.
A few years ago Kaspersky Lab launched its cloud service named Kaspersky Security Network, an early warning system for various types of new cyberthreats.Data from KSN allows Kaspersky Lab’s researchers to identify the most vulnerable and most attacked software. Overall, Kaspersky Security Bulletins are now based on data obtained and processed using the Kaspersky Security Network service.
It is actually an interactive visualization of data streams coming from KSN – threats detected with various diagnostic tools, including On-Access Scan, On-Demand Scan, Web and Mail Anti-Viruses, as well as the Vulnerability Scan and Intrusion Detection System.
Right now the Cyberthreats Realtime Map shows that Russia, India, Vietnam, USA and Germany are the top five most infected countries in the world.
CLICK HERE.> FOR CYBERTHREAT REAL-TIME MAPThere Are Hundreds of Enterprise Security Solutions WITH Commercial And Opensource Licenses Making It Difficult To Choose The Ones That Are The Best Fit For Your Situation.

SAST tests the application’s internal source code in early development phases to ensure developers follow the best security practices when writing code. In contrast, DAST testing begins in later development phases in a working application. It tests the application while it’s running to discover its susceptibility to the most common cyber threats.
Leveraging CSPM soutions is one of the most effective cloud security solutions.Encryption is one of the best ways to secure your cloud computing systems. There are several different ways of using encryption, and they may be offered by a cloud provider or by a separate cloud security solutions provider.
With a Zero Trust framework, no user, device, or network can be automatically trusted with access to company resources. This mindset relies on three core principles: assume breach, verify explicitly, and least privilege access. The Zero Trust framework is the opposite design pattern to the VPN.
A vulnerability scan is an automated, high-level test that looks for and reports potential known vulnerabilities. Vulnerability scans are able to identify thousands of unique external and or internal weaknesses that hackers can use to exploit in your cloud hosted enviroments. A penetration test is a detailed hands-on examination by a real person that tries to detect and exploit weaknesses in your system.